Help, help, I was hacked!
Heard 1000 times, thought 10,000 times, and yet never happened.
In the first case, we show a real hack, the "apparent" takeover of a domain with their web space. Webspace is the location on a server where the website and its associated Internet files, such as images, music, videos, and most importantly the necessary work files, are stored. Sometimes the internet files are also on foreign servers, but that does not matter for our topic.
Hacking simply means that the attacker has guessed the access password for the web space. This is done through continuous login attempts with hundreds of thousands or millions of different passwords. Frequently, hackers get the password through Trojans into infected emails containing alleged alerts and password checks from their own bank. As we like to use the same password for our various Internet activities for convenience, so-called master passwords, hackers often only have to steal the password of a social network to gain access to all password-encrypted institutions.
If the password was guessed by the webspace, then the hacker can change the entire website according to his wishes and ideas. The Internet files are replaced by the files of the attacker. Often hackers then invite hidden Trojans to the captured web space to infect the visitors as well and steal their own passwords to all sorts of portals and institutions. This means the Supergau, a kind of pyramid scheme, to do the greatest possible damage, or to steal the highest number of foreign passwords.
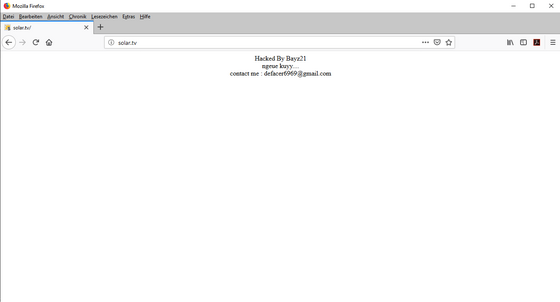
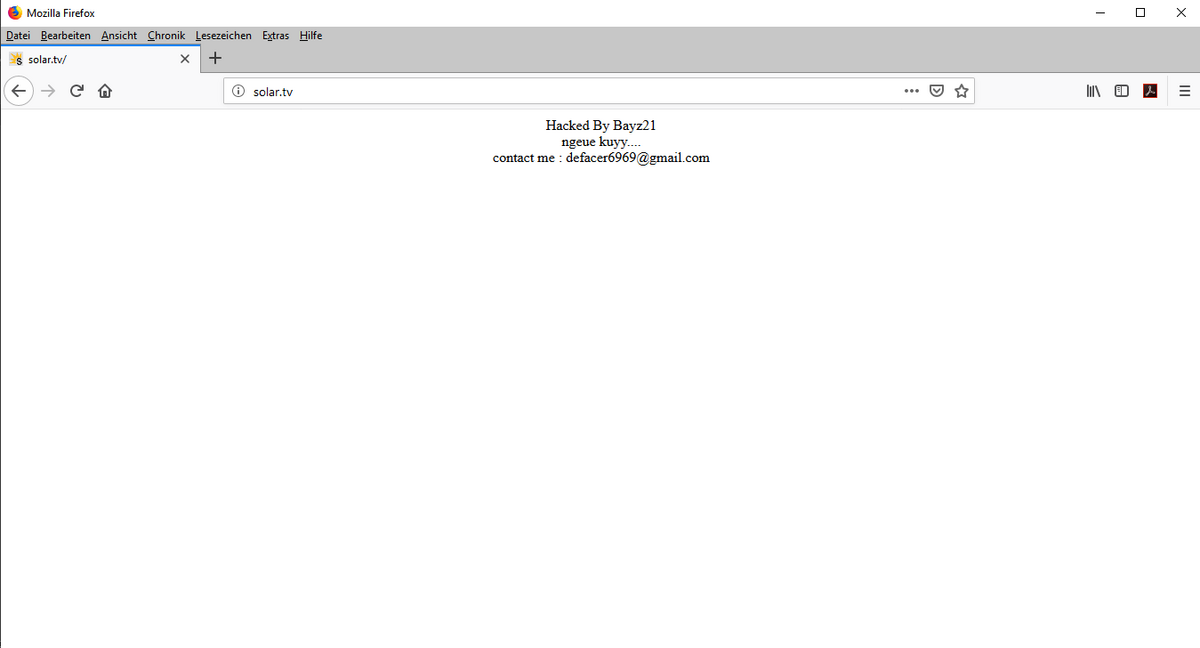
But let's just show the simplest way, namely a hacked webspace on the visible for all the world the home page of the domain was replaced by the hacker.
We must, or should assume, that the personal data, such as the e-mail address in the example shown, is not necessarily the real mail address of the attacker. Good hackers know they can be found by law enforcement agencies. But very good hackers use opportunities to retrieve emails through disguised, intricate paths, such as proxy servers, or stolen e-mail accounts. A quick tip: If you have actually and demonstrably hacked, so should, even if it is infinitely difficult to replace all their own access. Because with: "I was hacked, have changed my password, and now I'm sure" is the case by no means done. There is the visible, visible damage, but there are also the invisible consequential damages, of which one does not even have a spark of clue.
When I came across the hack presented here by chance, when I just wanted to see if the domain shown was already taken, otherwise I would have registered it, I started with various inquiries. For example, I wanted to know from which part of the world the attacker is coming. For this, I put the two words "ngeue kuy" in the Google translator and clicked on "language recognize". Translated, the two words mean "yesterday." In my opinion, this refers to the time of the crime, namely when the web space and the domain was taken over. But when was yesterday? We as simple site visitors are hereby already at the end of the search. Because we do not see the timestamp of the changed homepage. But at least we know that the hacker "seems" to speak Sundanese. Seems!
Because often attackers deliberately set the wrong track to lead pursuers astray. The same applies to the e-mail address! Often such tracks lead to the enemy of the attacker, whom he also wants to harm. In such a search, one should proceed with sharpened senses and high alert readiness. Because nothing is as it seems...
Show me who you are hacking, then I'll show you who you are!